Connecting remote IoT devices through a Virtual Private Cloud (VPC) using a Raspberry Pi has become a popular solution for secure data transmission. As the Internet of Things continues to expand, ensuring secure connections is more critical than ever. This guide will walk you through the process of setting up a secure connection using a Raspberry Pi, focusing on VPC configurations and providing a free download option for Windows users.
In today's interconnected world, IoT devices are transforming industries and households alike. However, with this rapid growth comes the challenge of maintaining secure communications between devices and networks. This article will explore the importance of secure connections, the role of VPCs, and how Raspberry Pi can be utilized as an affordable and efficient solution for remote IoT setups.
Whether you're a hobbyist, a small business owner, or an enterprise IT professional, this guide will provide step-by-step instructions, valuable insights, and practical tips to help you establish a secure IoT environment. By the end of this article, you'll have the knowledge and tools necessary to protect your IoT ecosystem effectively.
Read also:Are Kody And Robyn Still Together Exploring Their Relationship Dynamics
Table of Contents
- Introduction to IoT Security
- What is a VPC?
- Raspberry Pi as an IoT Gateway
- Setting Up a VPC for Remote IoT
- Securely Connecting IoT Devices
- Free Download Options for Windows
- Best Practices for Security
- Troubleshooting Common Issues
- Case Studies
- Conclusion and Next Steps
Introduction to IoT Security
IoT security is a critical aspect of modern technology. With billions of connected devices globally, ensuring secure communication is paramount. The keyword "securely connect remote IoT" emphasizes the importance of safeguarding data as it travels between devices and networks. In this section, we'll delve into the fundamental principles of IoT security and why it matters for both personal and professional use cases.
Why IoT Security Matters
IoT devices collect and transmit sensitive data, making them prime targets for cyberattacks. Without proper security measures, these devices can compromise not only personal privacy but also organizational integrity. Key considerations include encryption, authentication, and network segmentation.
- Encryption ensures data confidentiality during transmission.
- Authentication verifies the identity of devices and users.
- Network segmentation isolates IoT devices from critical systems.
What is a VPC?
A Virtual Private Cloud (VPC) is a private network within a public cloud environment. It allows users to securely host and manage their resources, such as servers and databases, without exposing them to the public internet. By incorporating a VPC into your IoT setup, you can enhance the security of your remote connections.
Read also:Hub4u Movie Download Your Ultimate Guide To Legal And Safe Streaming
Key Features of a VPC
VPCs offer several advantages for IoT deployments:
- Isolated network environment
- Customizable IP address ranges
- Flexible access control
- Integration with cloud services
These features make VPCs an ideal solution for securely connecting remote IoT devices.
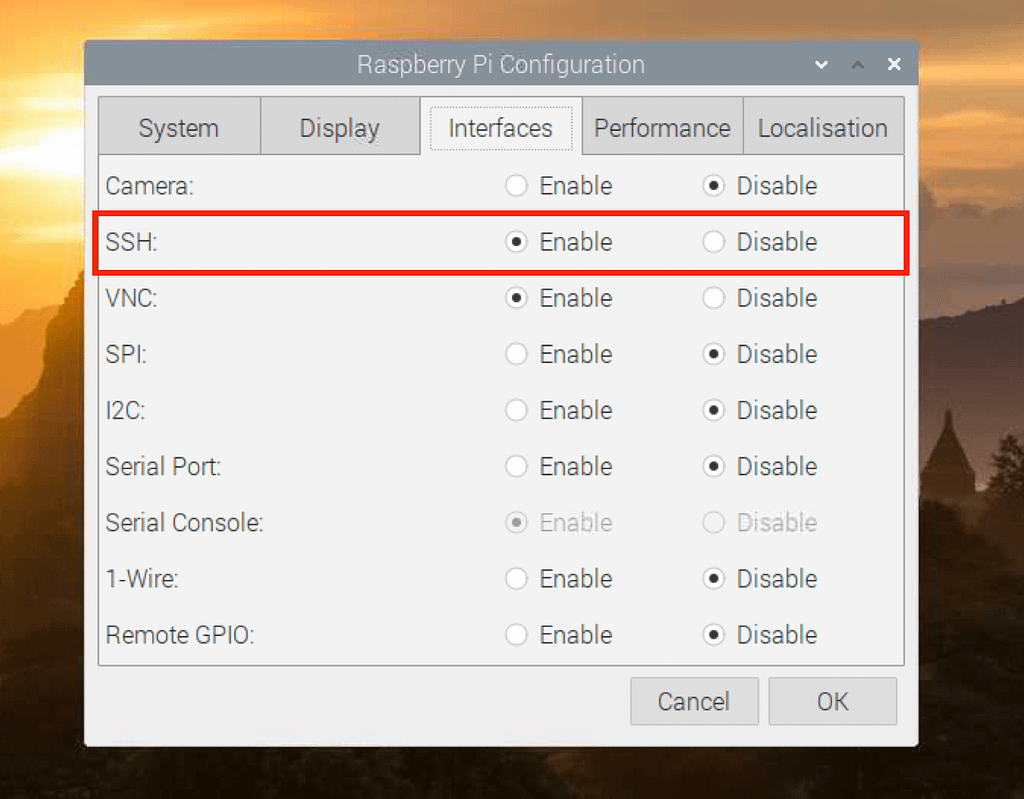
Raspberry Pi as an IoT Gateway
The Raspberry Pi has emerged as a versatile and cost-effective platform for IoT applications. Its compact size, low power consumption, and extensive community support make it a popular choice for hobbyists and professionals alike. When combined with a VPC, the Raspberry Pi can serve as a secure IoT gateway, facilitating communication between devices and the cloud.
Advantages of Using Raspberry Pi
Using a Raspberry Pi for IoT projects offers numerous benefits:
- Open-source software compatibility
- Wide range of available libraries and tools
- Scalability for small to large-scale deployments
- Customizable hardware configurations
These advantages make the Raspberry Pi a powerful tool for securely connecting remote IoT devices.
Setting Up a VPC for Remote IoT
Configuring a VPC for remote IoT involves several steps, including network planning, resource allocation, and security policy implementation. This section will provide a detailed guide to help you set up a VPC tailored for your IoT needs.
Step-by-Step Guide
Follow these steps to create a VPC for your IoT setup:
- Define your network requirements and IP address ranges.
- Create subnets for different device groups.
- Set up security groups and access control lists (ACLs).
- Integrate your VPC with cloud services for data storage and analysis.
By following this guide, you'll establish a secure and efficient VPC environment for your IoT devices.
Securely Connecting IoT Devices
Once your VPC is configured, the next step is to securely connect your IoT devices. This involves setting up authentication mechanisms, implementing encryption protocols, and monitoring network activity. In this section, we'll explore best practices for securing IoT device connections.
Best Practices for Secure Connections
To ensure secure connections, consider the following practices:
- Use strong passwords and multi-factor authentication.
- Enable SSL/TLS encryption for data transmission.
- Regularly update firmware and software to patch vulnerabilities.
- Implement intrusion detection systems (IDS) for real-time monitoring.
These practices will help safeguard your IoT devices against potential threats.
Free Download Options for Windows
For Windows users, there are several free tools and software available to facilitate secure IoT connections. These tools can help you configure VPCs, manage Raspberry Pi devices, and monitor network activity. In this section, we'll highlight some of the best free download options for Windows.
Recommended Tools
Consider the following tools for your IoT projects:
- PuTTY: A free SSH and Telnet client for remote access.
- WinSCP: A secure file transfer protocol (SFTP) client for managing files.
- Wireshark: A network protocol analyzer for monitoring traffic.
These tools, combined with your Raspberry Pi and VPC setup, will provide a comprehensive solution for securely connecting remote IoT devices.
Best Practices for Security
In addition to secure connections, implementing overall security best practices is essential for protecting your IoT ecosystem. This section will outline key strategies for enhancing the security of your IoT setup.
Strategies for Enhanced Security
Adopt the following strategies to improve your IoT security:
- Regularly audit your network for vulnerabilities.
- Limit device access to authorized users only.
- Use encryption for both data at rest and in transit.
- Stay informed about the latest security trends and threats.
By adhering to these strategies, you'll create a robust security framework for your IoT environment.
Troubleshooting Common Issues
Even with the best security measures in place, issues may arise during IoT deployments. This section will address common problems and provide solutions to help you troubleshoot effectively.
Common Issues and Solutions
Here are some common issues and their solutions:
- Connection problems: Check network settings and restart devices.
- Authentication failures: Verify credentials and update authentication policies.
- Performance bottlenecks: Optimize resource allocation and network configurations.
By addressing these issues promptly, you'll maintain a reliable and secure IoT setup.
Case Studies
Real-world examples can provide valuable insights into the practical application of secure IoT connections. In this section, we'll examine case studies from various industries to illustrate the benefits of using a Raspberry Pi and VPC for IoT deployments.
Case Study: Smart Agriculture
Agricultural businesses have successfully implemented IoT solutions to monitor crop health and optimize resource usage. By using a Raspberry Pi as an IoT gateway and configuring a VPC for secure data transmission, these businesses have achieved significant improvements in efficiency and productivity.
Conclusion and Next Steps
In conclusion, securely connecting remote IoT devices through a VPC using a Raspberry Pi is a powerful solution for modern IoT deployments. By following the guidelines and best practices outlined in this article, you can establish a secure and efficient IoT environment tailored to your needs.
We encourage you to take the following actions:
- Download the recommended tools for Windows to enhance your IoT setup.
- Implement the best practices discussed to strengthen your security measures.
- Share your experiences and insights in the comments section below.
- Explore additional resources and articles on our website for further learning.
Thank you for reading, and we wish you success in your IoT endeavors!